Phishing Scammers always use familiar company names or assume to be someone you
know get you to commit to their ends. Which is usually to collect your financial information. Police in Ohio
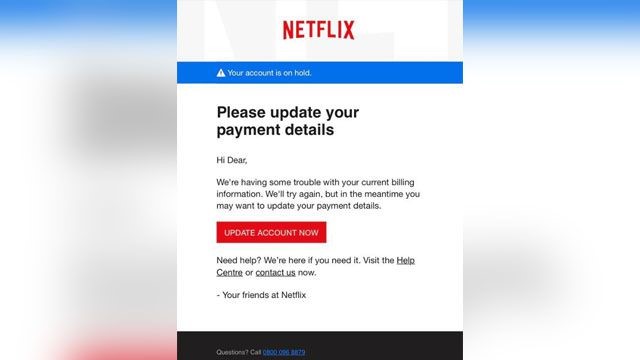
shared a screenshot of a phishing email designed to steal personal
information featuring Netflix. . The email claims the user’s account is on hold because
Netflix is “having some trouble with your current billing information”
and invites the user to click on a link to update their payment method.
From FTC;
Before you click on a link or share any of your sensitive information:

From FTC;
Before you click on a link or share any of your sensitive information:
- Check it out. If you have concerns about the email, contact the company directly. But look up their phone number or website yourself. That way, you’ll know you’re getting the real company and not about to call a scammer or follow a link that will download malware.
- Take a closer look. While some phishing emails look completely legit, bad grammar and spelling can tip you off to phishing. Other clues: Your name is missing, or you don’t even have an account with the company. In the Netflix example, the scammer used the British spelling of “Center” (Centre) and used the greeting, “Hi Dear.” Listing only an international phone number for a U.S.-based company is also suspicious.
- Report phishing emails. Forward them to spam@uce.gov (an address used by the FTC) and to reportphishing@apwg.org (an address used by the Anti-Phishing Working Group, which includes ISPs, security vendors, financial institutions, and law enforcement agencies). You can also report phishing to the FTC at ftc.gov/complaint. Also, let the company or person that was impersonated know about the phishing scheme. For Netflix, forward the message to phishing@netflix.com.
